What is a Black Box pen test?
A Black Box pen test is performed by ethical hackers to discover vulnerabilities in IT systems and networks before malicious attackers do.
A Black Box pen test is performed by ethical hackers to discover vulnerabilities in IT systems and networks before malicious attackers do.
What does a Black Box pen test actually entail?
Why do organizations conduct Black Box pen tests?
How are pen tests for web applications performed?
9 Benefits of Black Box Pentesting
3 Disadvantages of Black Box Pentesting
Black Box vs. Grey Box Vs. White Box Pentesting
A a total lack of information pentest, is a third-party testing service aimed at finding and exploiting vulnerabilities in a system as an outsider. In a Black Box pen test, no account information is provided, as well as little information about the target except perhaps an IP address, URL or building location. Essentially, then, the target environment is a "black box." This means the tester has no access to source code (other than publicly available code), internal data, structure and design of the system prior to testing.
The name "Black Box" refers to the dark premise of the test in which no prior knowledge is provided.
A Black Box pentest assesses a system at runtime. When the target system is an application, Black Box pentesting is also known as Dynamic Application Security Testing (DAST). A Black Box pen test is highly suitable for evaluating the security of external assets, such as:
While a Black Box pen test cannot be used as a replacement for a comprehensive security assessment, they help test an application or network from an end user or hacker's point of view. It can reveal serious vulnerabilities in your digital assets, such as validation errors, disclosure of information via error messages, incorrect server configurations, and so on.
Don't hesitate to contact us; we would be happy to tell you more about everything concerning Cybersecurity.

There are several reasons and use cases that can prompt an organization to opt for a Black Box pen test. Below we have listed the reasons why most of our clients have Black Box pen tests performed by us.
Black Box Pentesting is an excellent choice for companies looking to detect vulnerabilities early in the SDLC. This proactive approach allows them to address issues before they grow into serious security risks.
Companies operating in regulated industries such as finance, government or healthcare often need to conduct regular security assessments to meet compliance standards. Black Box Testing is a smart way to meet these regulatory requirements.
Regardless of industry regulations, regular security assessments, including the Black Box Test, are vital to confirm that your security posture remains robust and adaptable to growing cyber threats.
When you integrate third-party networks and applications into your infrastructure, it is important to critically examine their security. Black Box Test helps evaluate potential threats associated with these integrations.
Black Box Testing is excellent for simulating practical use cases and scenarios that could occur in the real world. It provides insight into how well your system can withstand threats from attackers operating under real-life conditions.
Black box testing is critical to application security because it offers certain advantages over other testing methods. However, the best results are only possible if an organization combines a Black Box pen test with a complementary testing method that analyzes the internal workings of a system, such as a Code Review. The benefits of Black Box pentesting include:
A Black Box pen test is an effective way to test the security of a system. However, it is not a substitute for a comprehensive assessment of the source code and internal workings of the system in question.
Because a Black Box test does not include internal testing, a system may falsely appear "secure" if the tester fails to find vulnerabilities in the external components. However, there may be several vulnerabilities lurking beneath the surface of the system that a Black Box pen test cannot figure out.
In other words, vulnerabilities found in a Black Box test indicate that the target system is inadequately secured. Yet this does not mean that a system is completely secure if the Black Box pen test fails to find critical vulnerabilities. In that case, the vulnerabilities may simply be hidden in internal systems.
In short, a Black Box pen test:
The amount of information shared prior to a pen test can have a huge impact on its results. The style of testing is usually defined as White Box, Grey Box or a total lack of information.
Using pentesters tools such as Nmap and Wireshark to examine target systems for vulnerabilities. Many of these tools provide preliminary information, which the tester must examine in more detail through manual testing.
Pentesters will also examine the network to detect open ports that an attacker could exploit to gain access to a network. These open ports are often the location of attempted exploits, as pentesters try to get past defenses such as firewalls.
Using an automated utility often used in "Brute Force" attacks, a tester attempts to log in within a system by using a list of commonly used passwords. The hope is to find a match, giving the tester access to the system through someone else's credentials.
Social engineering is convincing a legitimate system user to hand over sensitive information - such as login credentials - by impersonating a trusted person or party. Phishing is one of the most commonly used techniques, but other techniques are also used by pen testers.
In syntax testing, pentesters use the format of data input to find vulnerabilities. In the simplest terms, the goal is to examine outcomes when they use input that is outside syntax to see if they are useful to invade a system.
Fuzzing is based on injecting noise, which allows the pentester to examine Web interfaces and discover missing input controls. If unusual behavior is the result, it may indicate incorrect software controls, which could potentially be exploited.
A typical Black Box pen test includes the following 5 stages:
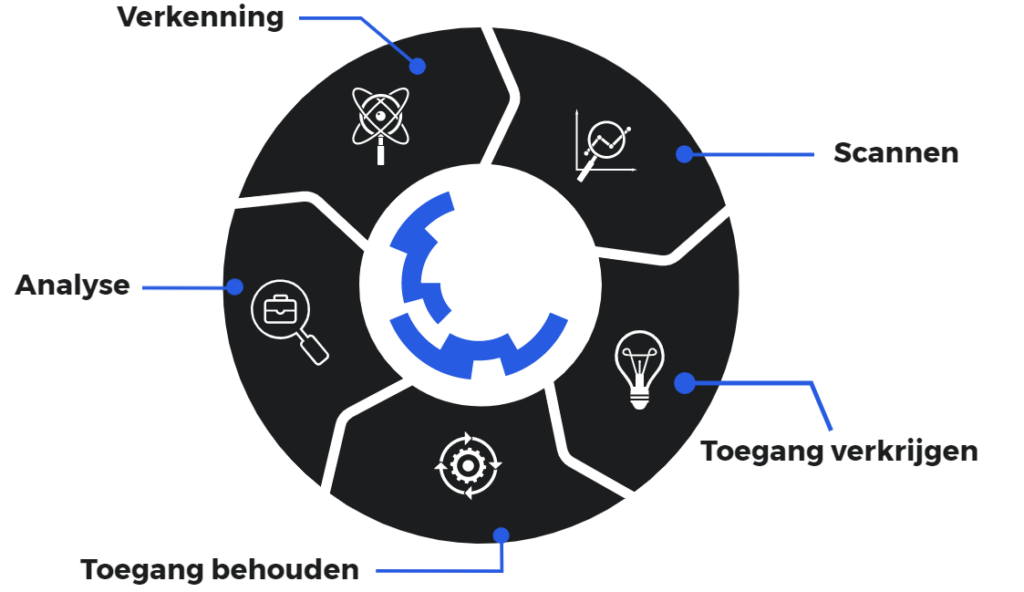
Obtaining information is an important first step in assessing a target's security. Pen testers consult a variety of sources, both public and private, to develop a thorough attack strategy. These sources include online searches, domain registration data, social engineering techniques, non-intrusive network scans and, in some cases, even "dumpster diving." This acquired data allows our pen testers to map the target's attack surface and identify potential weaknesses.
Pentesters use sophisticated tools to examine the target, such as a Web site or system, for possible vulnerabilities. This includes investigating open services, detecting security problems in applications and detecting vulnerabilities in open-source components. Exactly which tools are used depends mainly on the findings during the initial exploration of the target system.
Attackers have diverse motives, ranging from stealing, modifying or deleting data to moving financial resources or even harming an organization's reputation. For each test, the pen testers select the most appropriate tools and techniques to gain access to the system, whether through known vulnerabilities such as SQL injection, malware, social engineering, or other methods.
Once access to the target is gained, it is essential to continue the simulated attack to achieve the ultimate goal. This may include exfiltrating data, altering system functionality or misusing privileges. The goal is to demonstrate the potential impact of such attacks.
Upon completion of the pen test, the findings are carefully analyzed, resulting in an actionable report. The report documents vulnerabilities in detail and places them in the context of the organization, allowing the identified security risks to be effectively addressed.
A full Black Box pen test performed by real ethical hackers usually costs between €5,000 and €50,000 per test. A Black Box pen test from Warpnet costs a minimum of €2,400, however, the exact cost can vary based on the scope of the assignment and its objectives.
Black Box pen tests are generally cheaper than Grey Box and White Box pen tests, due to the comparatively limited scope and duration of a Black Box pen test.
Common tools used for black box pen testing include: