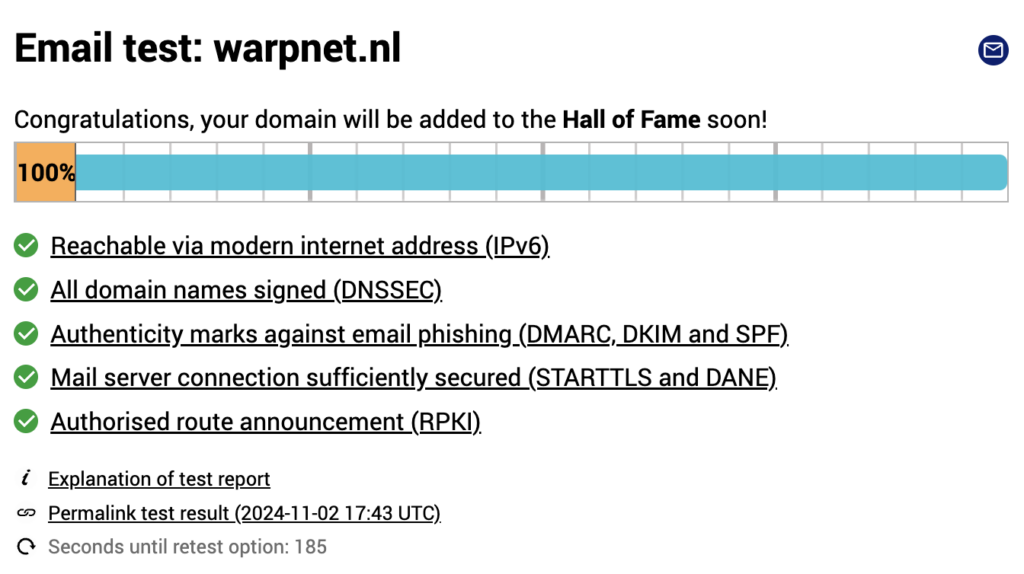
Looking for ways to improve the security of your e-mail traffic? Microsoft announced in October full support for the email security standard DANE on Exchange Online. This also gave existing Exchange Online customers the ability to enable the additional security options.
As of early 2022, Microsoft is already offering support for DANE on outgoing mail, but the support on incoming mail has been a while in coming. Although this option has now become available, much of the configuration cannot be put through Microsoft's web portal, instead it must be done using various PowerShell cmdlets.
To configure SMTP DANE with DNSSEC for incoming mail on Exchange Online, there are a number of steps that need to be completed:
- Update the Time To Live (TTL) value of the existing MX record to the lowest possible value. Then wait at least the length of the previous TTL value before implementing the next step. If the previous TTL value was at, say, '3600 seconds' or '1 hour' before it was changed, you should wait at least 1 hour before performing step 2.
- Connect to Exchange Online via the Connect-ExchangeOnline cmdlet by entering in PowerShell the command
Connect-ExchangeOnlineexecute. - To use SMTP DANE with DNSSEC, DNSSEC must first be enabled. This can be done using the Enable-DnssecForVerifiedDomain cmdlet. For warpnet.co.uk the command looks like this:
> Enable-DnssecForVerifiedDomain -DomainName "warpnet.co.uk"
DnssecMxValue Result ErrorData
------------- ------ ---------
warpnet-en.s-v1.mx.microsoft Success- Use the DnssecMxValue value to create a new MX record on the domain. Make sure it gets a priority value of 20 and uses the lowest possible TTL value.
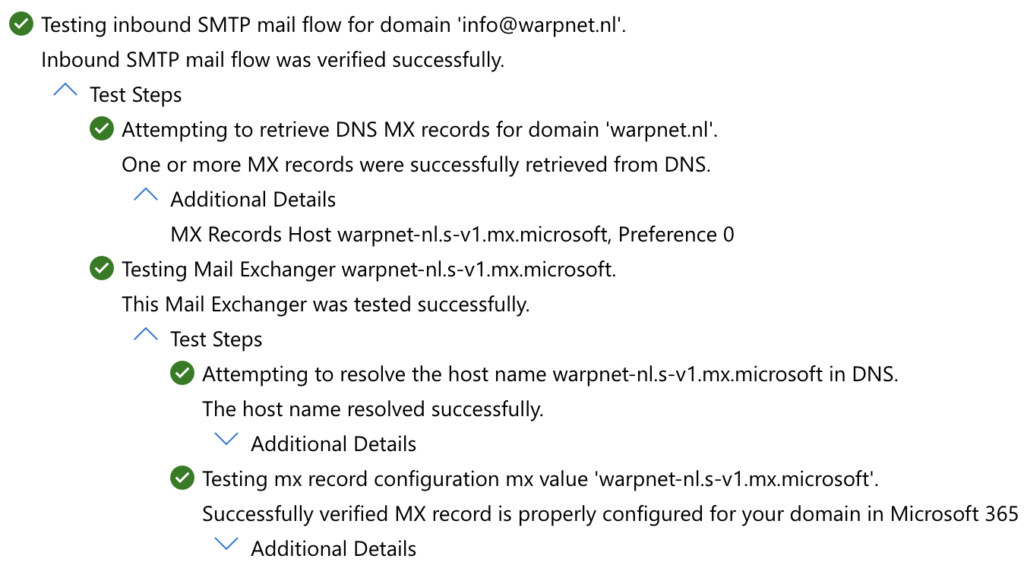
- Verify that the newly configured incoming mail server is working correctly by using the Inbound SMTP Email Test from Microsoft. Unfolding the test steps reveals whether the new Mail Exchanger on the domain is mx.microsoft works correctly as shown in the screenshot below.
- Delete the old MX record which ends in mail.protection.outlook.com, mail.eo.outlook.com or mail.protection.outlook.de. Next, the TTL value of the MX record ending in mx.microsoft can be changed to 3600 seconds or 1 hour.
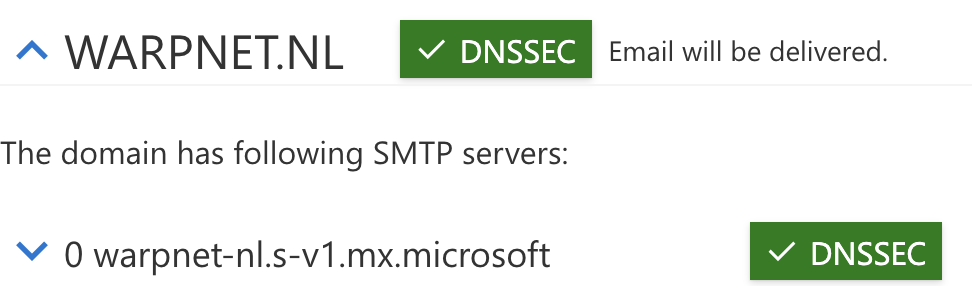
- Verify that everything is working correctly by running the DNSSEC Validation test in the Remote Connectivity Analyzer from Microsoft for the domain as shown in the screenshot below.
- Once DNSSEC is enabled, SMTP DANE can also be used on the incoming mail server. To configure this, the Enable-SmtpDaneInbound cmdlet. For warpnet.co.uk the command looks like this:
> Enable-SmtpDaneInbound -DomainName "warpnet.co.uk"
Result ErrorData
------ ---------
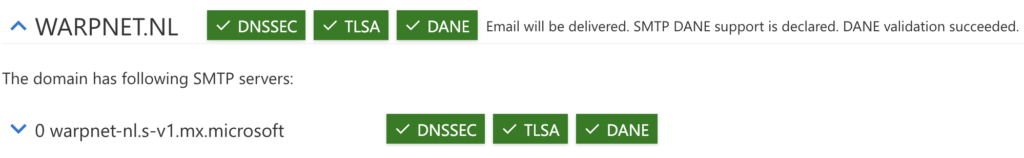
Success- Verify that both DNSSEC and SMTP DANE records (TLSA) are correctly configured by DANE Validation (including DNSSEC) test in the Remote Connectivity Analyzer from Microsoft for the domain as shown in the screenshot.
The configuration for SMTP DANE with DNSSEC on the incoming mail server of Exchange Online should now be successfully implemented. Optionally you can use the e-mail test of internet.co.uk. This also shows possible other areas of improvement regarding the use of IPv6, DMARC, DKIM and SPF as shown in the following screenshot.